Altair IoT Studio Specifications
Get an overview of the features included in the General Release of Altair IoT Studio.
General Release
For information on installation and upgrade procedures, as well as details on supported platforms and software requirements, contact us. For registration, visit swx.altairone.com.
The Altair IoT Studio platform provides everything you need to quickly build scalable, secure, and smart connected ecosystems. It includes:
- Connecting your assets to the internet to transmit and store data in the cloud
- Building software backend to provide automation and coordinate data
- Simplifying the development of an application frontend using our dashboarding tools to analyze and show the information, and provide control
- In some cases, developing the automation at the edge to reduce latency and minimize data transport costs
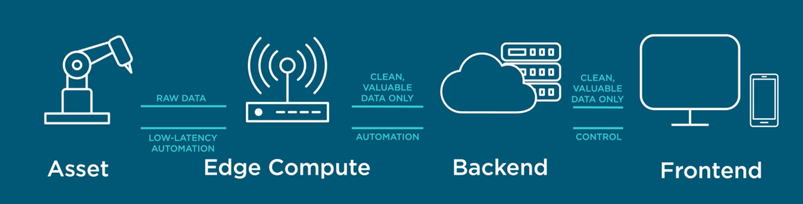
- For connecting the assets, it offers:
-
- IoT device modeling, connectivity and control: Model any asset and communicate with it in real time
- Specialized databases for IoT metadata and telemetry: Store your entire assets’ data
- For the Backend, it offers:
-
- Tools for filtering and processing the data fast.
- Serverless function engine to implement automation and business logic.
- Role-based access control services: Onboard thousands of users and easily control access
- For the Frontend, it offers:
-
- Drag and drop dashboard authoring tool to quickly create analytics visualization to share with your team
- For the Edge it offers:
-
- Specialized toolset for developing, deploying, and monitoring automation at the edge
Altair IoT Studio ensures security and performance from the beginning, helping the user to create scalable, secure IoT and analytics projects faster with smaller teams, and deploying everywhere. It connects seamlessly to Altair’s simulation and data analytics tools, which will help create digital twins.
Platform Capabilities
- Altair IoT Studio
-
- Consists of different modules that can be customized as needed
- Is based on a microservices architecture that makes it scalable and resilient to failure
- Is already optimized for performance, scale and security.
- Security
-
- Access to the Platform from the external world (the Internet) is encrypted
- Every request must come with a token (Oauth2), which in turn is obtained when users are correctly validated and authenticated
- Network Policies are implemented internally to control the traffic between different elements of the platform
- A threat detection engine runs internally to detect unexpected behavior and intrusions in real time